PGP
(OpenPGP) is the open standard that defines how PGP works. It provides email encryption and digital signatures, similar to S/MIME. OpenPGP uses key pairs: a public key and a private (secret) key. Public keys can be signed by other keys to indicate trust, although in practice most keys are only self-signed. Public keys can be uploaded to public key servers so others can find them, and they can be downloaded from those servers when needed.
OpenPGP offers two encoding methods: PGP/MIME and PGP/INLINE. PGP/MIME encrypts and signs the entire email message and works well with HTML email. PGP/INLINE handles each part of the message separately, which means HTML support is limited and not all email clients can use it. Because PGP/INLINE must process every part of the message, it can require more system resources. For most users, PGP/MIME is the more compatible and straightforward choice, especially for HTML emails.
Note
We recommend using PGP/MIME because it preserves the original message structure, fully supports HTML content, and provides better performance.
PGP keyring
The PGP keyring contains all your public and secret keys. Any key that has a corresponding private key is marked with a green lock icon in the first column.
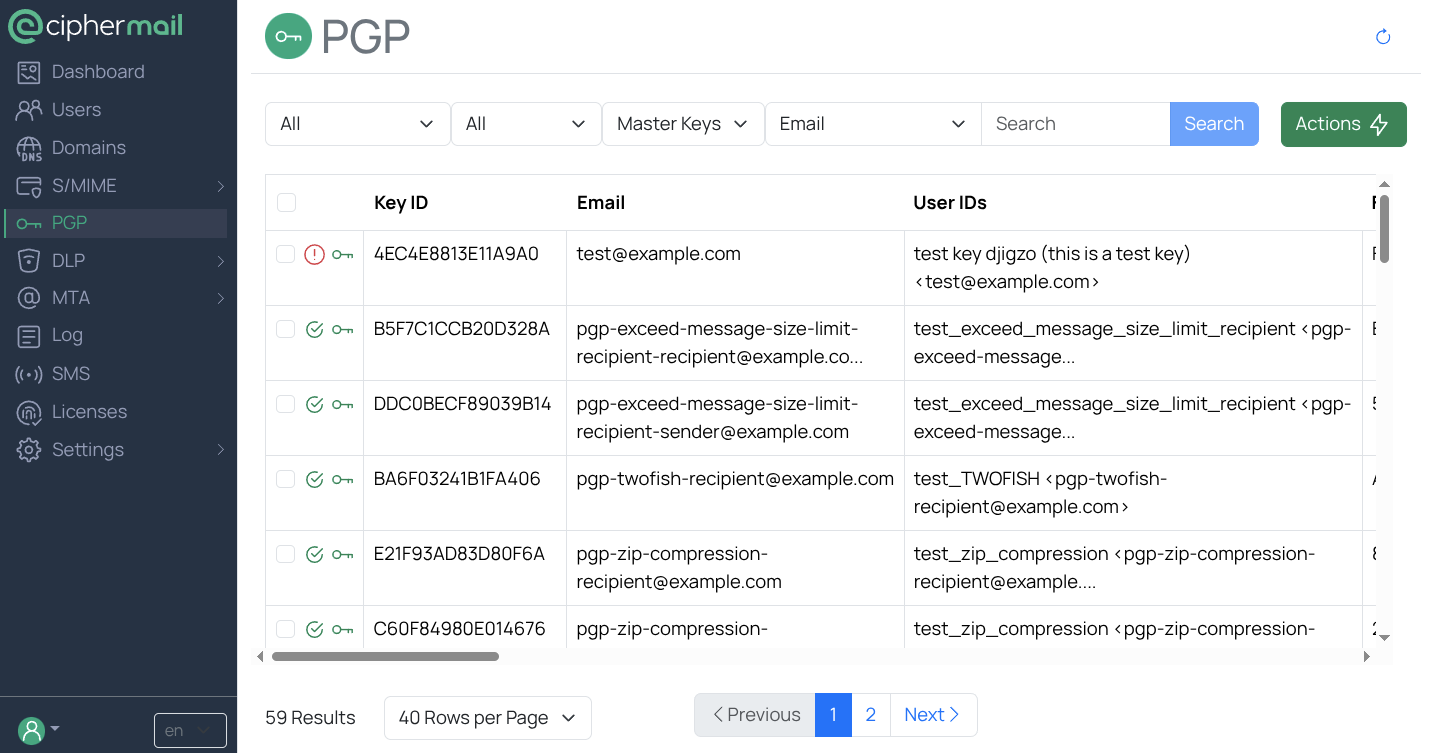
A PGP key is made up of two parts: a public key and a secret (private) key. The public key is shared with others so they can encrypt messages to you and verify your signatures. The secret key is kept private and is used to decrypt messages and create digital signatures.
Most users have a master key and one or more subkeys. The master key identifies the owner and includes the User ID, which typically contains the owner’s name and email address. The master key also signs the subkeys to show they belong together. Subkeys are often used for everyday tasks like signing or encrypting, while the master key is kept more secure.
Each key or subkey can be designated for signing, for encryption, or for both, depending on how you want to use it.
Click a row in the keyring table to open the PGP key’s details page, which includes all subkeys.
Caution
Never share your PGP secret keys with anyone outside your organization. For enhanced protection, store secret keys on a Hardware Security Module (HSM).
- Key ID
The Key ID uniquely identifies a key. It is available in two formats: a long Key ID and a short Key ID. The long Key ID is derived from the lower 64 bits of the key’s fingerprint, while the short Key ID uses the lower 32 bits.
- Example:
A key with for which the fingerprint is
4F1F836B90C074C7984285BC8277F1C27BBF6E41has a long of “Key ID”8277F1C27BBF6E41and a short of “Key ID”7BBF6E41
Caution
Do not use short Key IDs. Identifying a key by its short ID is no longer considered secure because different keys can share the same short ID. Attackers can intentionally create keys that collide with an existing short ID.
The Email field lists all addresses linked to user IDs, plus any additional addresses that an administrator has added manually.
- User IDs
The User IDs field lists all user IDs associated with the primary key. Typically, a user ID includes the user’s name and email address, but this is not required; it can contain any text.
- Fingerprint
The fingerprint is a 160-bit SHA-1 hash derived from the key. It serves as a unique identifier for that key.
- Sha256 Fingerprint
The Sha256 fingerprint is a unique identifier for a key, generated by computing its SHA-256 hash.
Tip
The OpenPGP standard defines fingerprints using SHA-1. For stronger security and to ensure the key remains uniquely identifiable even if SHA-1 becomes insecure in the future, use the SHA-256 fingerprint.
- Creation Date
The date the key was created.
- Expiration Date
Optional expiration date for the key; after this date, the key is no longer considered valid.
- Private Key Alias
The alias under which the certificate is stored in the keystore.
- Valid for encryption
Set to True if the key is valid for encryption. Set to False otherwise.
- Valid for signing
Set to True if the key is valid for signing. Set to False otherwise.
- Insertion date
The date the key was added to the keyring.
- Key length
The length of the PGP key.
- Algorithm
The PGP key algorithm is the cryptographic method used by a key to perform operations such as encryption and digital signing. It defines how the key is generated and what it can be used for, for example, encryption only, signing only, or both. Common algorithms include RSA, Elgamal, DSA, ECDH, ECDSA, EdDSA, and Diffie-Hellman.
- Master key
Set to True if the key is a master key. Set to False otherwise.
- Parent ID
The database ID that holds the parent (master) key.
- Valid
Indicates whether the key is trusted. Set to True if the key is valid (for example, not expired or revoked); set to False if it is not trusted.
- Failure message
If the key is invalid, the failure message includes additional details to help you identify and resolve the issue.
- ID
The database ID that holds the key.
Key trust
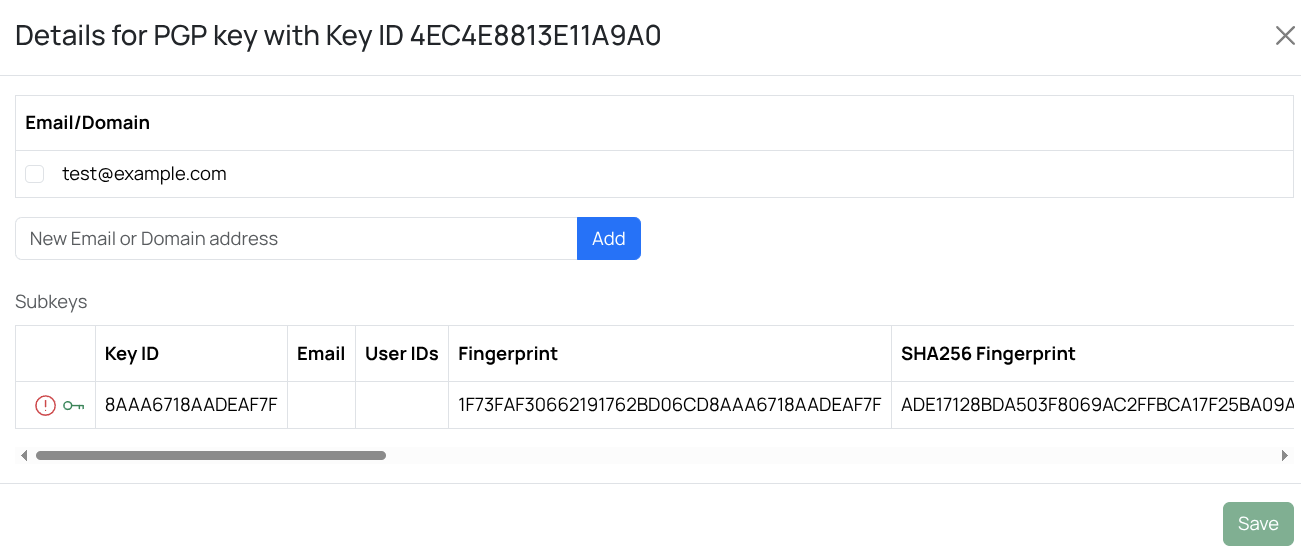
When you import PGP keys, they are not trusted automatically. In the key list, untrusted or invalid keys are shown with a red exclamation mark icon.
The trust of a key can be managed by selecting a key and then select Trust or Distrust.
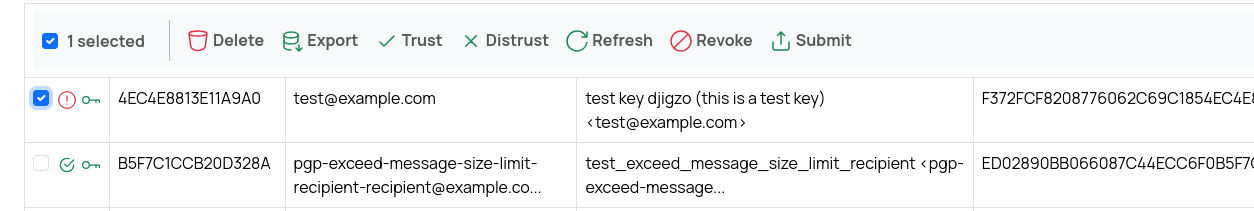
Publish keys
When you click Submit, all selected public keys will be published to the configured public key servers.
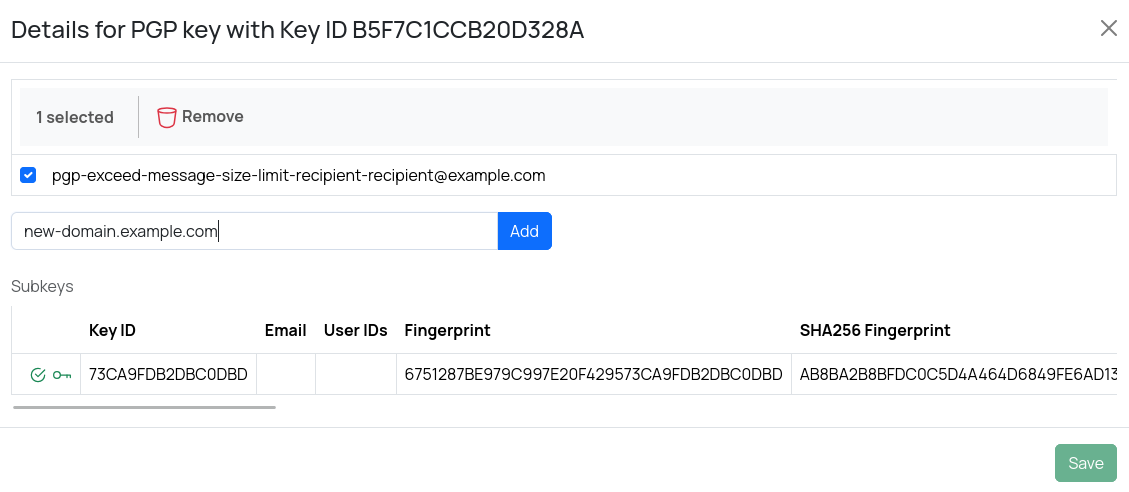
User ID
The User ID of a master key typically includes one or more email addresses associated with that key. You can manually add additional email addresses to a PGP key. You can also associate a domain with a PGP key. When a domain is associated with a PGP key, the key is considered valid for any email address within that domain.
To manage the associated email/domain addresses, click a key and add or remove additional email addresses or domains.
Tip
Associating a domain with a key, can be used for PGP domain to domain encryption
Revoke keys
To revoke a selected key, click Revoke from the selection menu. You can only revoke keys whose secret key is available.
Note
After revoking a key, submit the revocation to the key servers so they mark your key as revoked.
Import keys
You can import existing public and secret PGP keys from a file by selecting . If the secret keys file is password-protected, you will be prompted to enter the password to complete the import.
- Ignore parsing errors
A single file may contain multiple secret and public key rings. If Ignore parsing errors is enabled, the import process will skip any keys that cannot be imported due to issues such as corrupted data or non-standard formats, and continue importing the remaining keys.
Export keys
To export public and private PGP keys from your keyring, select the keys you want to export, then choose Export from the selection menu.
Create keyring
To create a new master key and subkey, click .
- Email address
The email address part for the “User ID”.
- Key type
The type of the key to generate
- Name
The name part for the “User ID”.
Find keys
You can store public keys on external key servers. This makes it easier for recipients to find keys for users outside your organization. To search for keys, open the Search keys page by selecting . The default configured keyserver is https://keys.openpgp.org.
Tip
The keyserver configuration can be managed with the pgp keyserver cli commands:
ciphermail-cli pgp keyserver get config
ciphermail-cli pgp keyserver set config --key-server-urls <url>
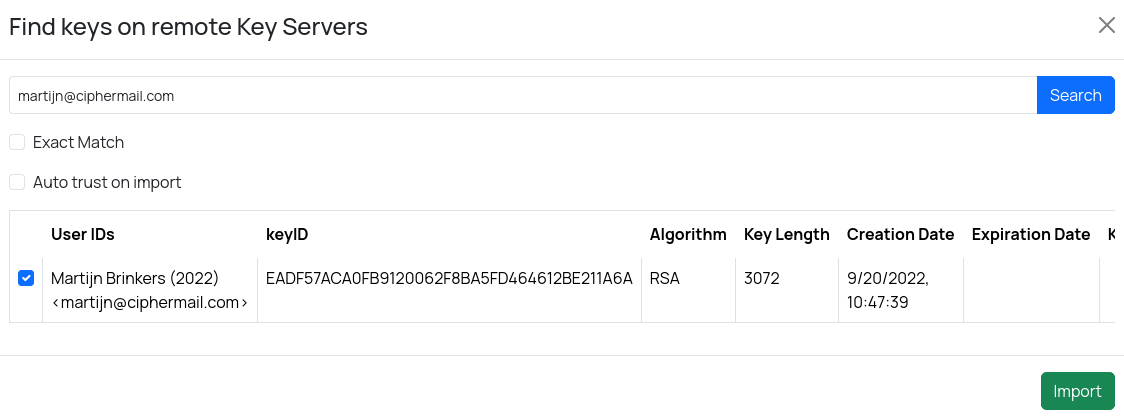
If any keys are found, you can select the ones you want and import them.
Tip
When searching by Key ID, include the 0x prefix before the search value
- Example:
Searching for a key with short “Key ID”
271AD23B, use the search string0x271AD23B
- Exact Match
When selected, the results will include only items that exactly match your query.
- Auto trust on import
If enabled, imported keys will be trusted automatically.
Key selection
The gateway automatically selects the appropriate keys for encryption and for signing, so you do not need to choose them manually. Whether a key is used for encryption or signing depends on several factors. The eligibility requirements for encryption keys differ from those for signing keys.
Encryption key selection
A key is used for encryption only if it meets all of the following requirements:
The key must be trusted
The key must not be expired
The key must not be revoked
The email recipient must match an associated email address or domain of the key
The key must be valid for encryption
The system automatically selects an encryption key for each recipient. To see which key is chosen for a specific recipient, open the PGP Keyring page and search by their email address or domain.
To check which encryption key is selected for a recipient or a domain, open the settings for the user or domain, then open the PGP menu and choose . The PGP Encryption Keys page shows the keys selected for the recipient or, if you selected a domain, for that domain. If more than one valid key is available for a recipient, the email will be encrypted with all of those keys.
Signing key selection
A key is used for signing only if it meets all of the following requirements:
A private key must be available
The key must be trusted
The key must not be expired
The key must not be revoked
The from sender address must match an associated email address or domain of the key
The key must be valid for signing
To check which encryption key is selected for a recipient or a domain, open the settings for the user or domain, then open the PGP menu and choose . The PGP Signing Keys page shows the key selected for the sender.
Only the selected signing key is used for signing. If multiple eligible signing keys are available, you can choose a different key by selecting it and applying the settings.