Webmail Messenger 
CipherMail Webmail Messenger is a secure webmail add-on for the CipherMail portal. If a message must be encrypted but S/MIME, PGP, or encrypted PDF delivery is not available, the message is delivered to a protected mailbox on the Webmail Messenger portal instead of your regular inbox.
Receiving email:
When a protected message is sent, the external recipient receives a notification email that includes a secure link to the Webmail Messenger portal.
When a recipient signs in to the portal for the first time, they will be prompted to create a password.
After setting a password, the recipient can sign in with their email address and the new password to view the message.
For added security, you can enable two-factor authentication (2FA) using a time-based one-time password (TOTP) app.
Reading and replying:
After you sign in, you can view the secure message in your web browser and download any attachments.
You can send a secure reply directly from the portal.
You can access Webmail Messenger from any modern web browser on desktop or mobile; no special software or certificates are required.
After you sign in, your Inbox opens. From there, you can read emails, delete them, and send replies:
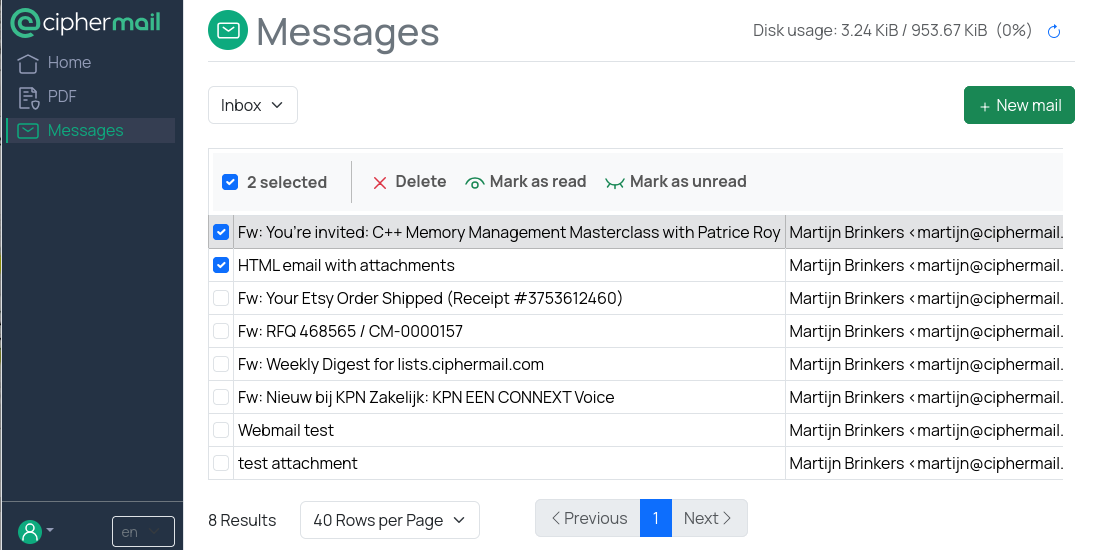
Features:
Automatically adapts to small screens, including smartphones.
HTML support
Full Unicode support
2FA using a time-based one-time password (TOTP) app
When enabled in your settings, you can compose replies and create new emails
Automatic cleanup of emails older than a chosen retention period
Quota management to control how much storage each user can consume
Configurable read receipts notify you when a recipient opens your message
You can download the email as a MIME-formatted .eml file
Hint
Use Auto cleanup to automatically remove emails after a set amount of time. When enabled, messages that exceed the retention period you select are deleted from Webmail Messenger to help conserve storage and keep your mailbox tidy. Choose the time limit that fits your needs. Note that once messages are removed by Auto cleanup, they are no longer available in Webmail Messenger.
Example of an email as it appears in the Inbox:
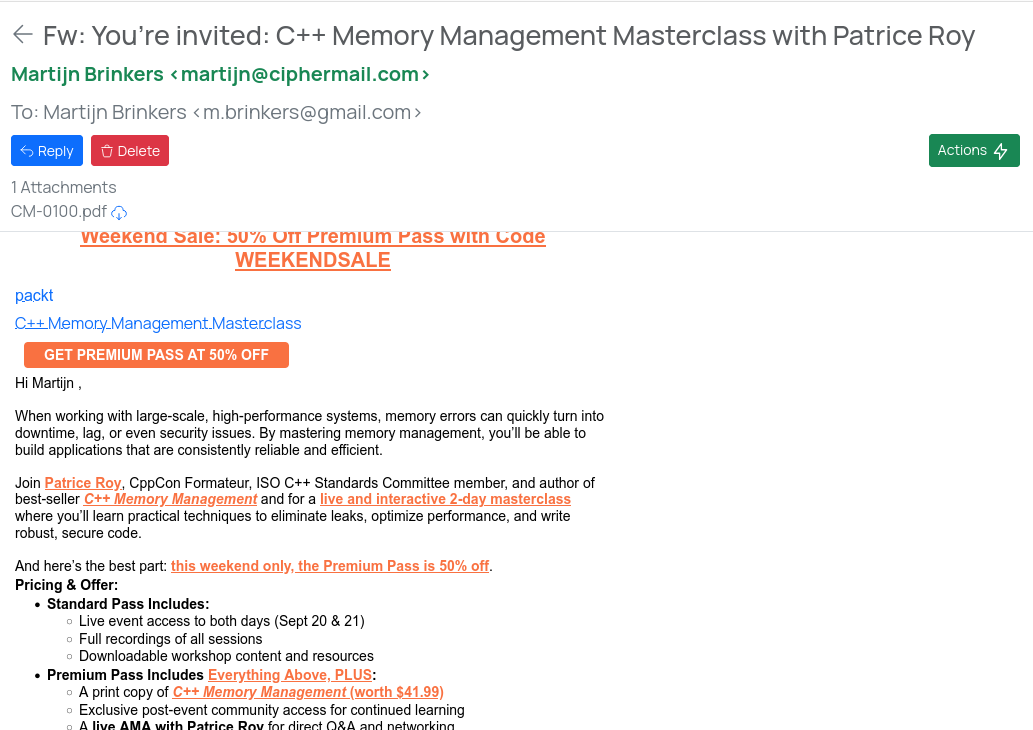
For more information on how to setup Webmail Messenger checkout the following links:
Encrypted storage
Webmail Messenger saves your email locally on your device’s file system. Access to these locally stored messages is restricted to the back-end application. For additional protection, you can enable S/MIME encryption for local storage. This encrypts your messages on disk so they remain unreadable if someone gains access to the storage outside the application. This is especially recommended when email is stored on a network drive, an external or removable drive, or any remotely mounted device.
To enable encrypted storage, follow these steps:
Encryption certificate
Encrypted storage requires a certificate and private key.
To generate a self-signed certificate and private key, execute the following command:
/opt/ciphermail/scripts/cm-generate-smime-cert.sh --email <email> --out-basename webmail-encryption
Replace the placeholder <email> with a valid email address. This email
address is for information only and is not used by the system.
Choose a strong password for your private key and store it in a secure location. You will need this password later.
Move the private key and certificate to /etc/ciphermail/private/:
sudo mv webmail-encryption.* /etc/ciphermail/private/
Tip
Make a backup of your private key and its password, and store them in a secure, preferably offline, location.
Private key unlock
Encrypted webmail messages are automatically decrypted when a user opens them. Decryption uses a private key that is protected by a password. Because the portal back-end must use this private key, it needs access to the password when the service starts. There are two ways to provide the password to the back-end service, each with its own trade-offs.
Option 1: store the password in an environment file. The file should be readable only by the root user and is read during startup of the portal back-end. The advantage is convenience and uptime: the service can start and restart without manual intervention, so users can access webmail immediately after a reboot or recovery. The downside is risk concentration: if someone gains root access to the gateway, they could extract both the private key and its password.
Option 2: require an administrator to enter the password at restart. With this approach, the password is not stored locally. This reduces exposure if the system is compromised. The trade-off is availability: the portal back-end will remain unavailable until an administrator unlocks the private key after each restart or reboot.
choose the option that matches your risk profile and operational needs. If maximum security is required and occasional administrator intervention is acceptable, use the manual unlock approach. If continuous availability and unattended restarts are more important, use the environment file approach and strictly control root access, file permissions, and audit procedures.
If you store the password in an environment file, ensure it is owned by root, has restrictive permissions, and is protected by your backup, logging, and access-control policies.
If you choose manual unlock, plan maintenance windows and on-call coverage so the service can be promptly unlocked after reboots or updates.
Document the chosen method so administrators know what to expect during restarts.
Option 1: store the password in an environment file
Create and Ansible override file at /etc/ciphermail/ansible/group_vars/all/override.yml.
---
ciphermail_backend__spring_active_profiles: 'webmail-encrypted-storage'
ciphermail_portal_backend__spring_active_profiles: 'webmail-encrypted-storage'
ciphermail_portal_backend__system_password: '<password>'
Replace the password placeholder with the private password you chose in the previous step.
Option 2: require an administrator to enter the password at restart
Create and Ansible override file at /etc/ciphermail/ansible/group_vars/all/override.yml.
---
ciphermail_backend__spring_active_profiles: 'webmail-encrypted-storage'
ciphermail_portal_backend__spring_active_profiles: 'webmail-encrypted-storage'
With option 2,
Run playbook
To apply the changes, run the playbook:
sudo cm-run-playbook
After applying the changes, the portal back-end will be restarted.
Check the portal back-end log
sudo journalctl -u ciphermail-portal-backend -f
With Option 1, the private key should be decrypted automatically after the restart.
With Option 2, the following message will be shown on the console:
Password entry required for 'Enter the CipherMail Portal System Password' (PID 478962).
Please enter password with the systemd-tty-ask-password-agent tool.
The portal back-end log file should contain the following line:
INFO Waiting for systemd password agent
To unlock the private key from the command line, execute the following command:
sudo systemd-tty-ask-password-agent
When prompted, enter your private key password. After the password is verified, the private key will be unlocked and the backend startup will continue.
If you enter an incorrect password, you will be prompted to try again. For troubleshooting, the portal back-end log will include the message: systemd-ask-password failed with exit code: 1.
After you turn on encrypted storage, all new emails will be stored in encrypted form. Existing emails will remain unencrypted.
Tip
Emails are encrypted using all certificates stored in
/etc/ciphermail/private/webmail-encryption.pem. If you add additional
certificates to this file, the email will also be encrypted with those
certificates. This allows you to encrypt messages with a key escrow
certificate for recovery or compliance purposes.